- Why should you care about how to improve API security?
- Business benefits of APIs
- Why hackers love APIs
- The key elements of API security design which differentiates them from traditional security
- The top API security risks and how to mitigate them
- 1. Insecure pagination
- 2. Insecure API key generation
- 3. Accidental key exposure
- 4. DDoS attacks
- 5. Wrong server security
- 6. Insufficient logging
- 7. Not handling authorization
- Appinventiv checklist of API security best practices
- 1. Find vulnerabilities
- 2. Use OAuth
- 3. Use tokens
- 4. Data encryption
- 5. Use rate throttling and limiting
- 6. Use API gateway
- 7. Use service mesh
- 8. Zero-trust formula
- 9. Validate parameters
- 10. Build a threat model
- Parting notes
Powered by a massive rise in microservices and the constant push to deploy applications quickly, APIs have become a go-to name for every entrepreneur.
However, with every small feature getting linked with other software or products for a seamless user experience, APIs are increasingly becoming a hub for security hacks. So much so that the How to Build an Effective API Security Strategy report by Gartner predicts that by 2022, API security risks will be one of the most frequent attacks leading to data breaches.
But what makes having an API security strategy a must-have for modern day entrepreneurs? Why is the technology given special attention? Will find out answers to these and how to mitigate API security risks in this article.
Why should you care about how to improve API security?
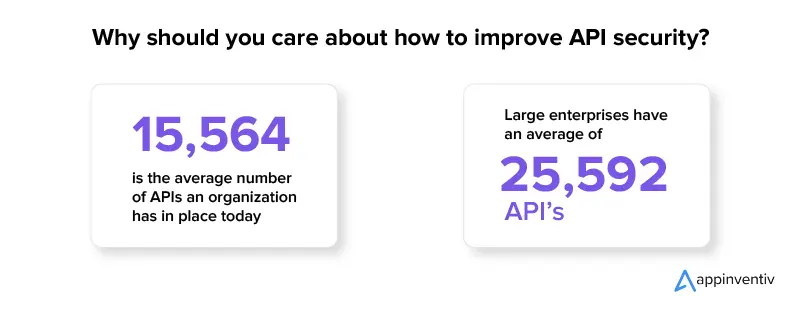
APIs help businesses become truly digital. No matter what your application is, an Application Programming Interface (API) connects it with other software or functionality – saving the time in building them from scratch.
Now the reason why APIs are given special focus is because of the level of impact they carry in a business’s success.
Business benefits of APIs
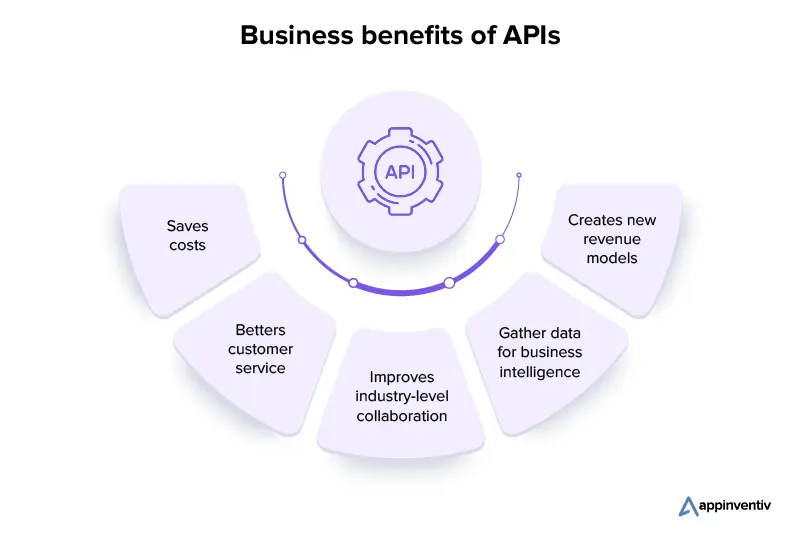
Saves costs: As APIs enable businesses to make use of the functions and data of other companies, it cancels out the need to create those features in-house. An event that helps save the software development cost to a great extent.
Betters customer service: By linking multiple software, API offers businesses a well-rounded view of their customers and what they are looking for. This information helps the company interact with their consumers better and make informed decisions.
Improves industry-level collaboration: API enables businesses to connect with other companies across industries, who can help make the online services and platforms robust. This, in turn, betters the partnerships, creates new business opportunities, and better the efficiency of the business’s operations.
Gather data for business intelligence: Businesses can make use of API for collecting their customers’ preferences and behavior. This information is then analyzed for an in-depth understanding into current market trends and customers’ needs.
Creates new revenue models: API gives businesses multiple platforms to promote and sell their services, digital products to. Through the model, businesses can do anything from selling data to other companies to building new software on the basis of existing APIs.
The benefits of APIs in a business are manifold. But so are the API security risks. There are two primary reasons why hackers love testing a company’s API security design.
Why hackers love APIs
- An easy way to get access to company data – APIs gives hackers direct access to stored data, including sensitive information, via multiple software programs.
- An easy mode of bypassing security measures – A number of companies use firewalls to save their system from hackers. However, a less thought of API security strategy can make it easy for the hackers to enter the software through this backgate.
So here are the pros and cons of APIs that lead to a special attention from the web app QA team.
Now, I am sure you must be wondering why the list of API security best practices is different from that of traditional security. Let’s answer that next before we look into the top API security risks and how to mitigate them.
The key elements of API security design which differentiates them from traditional security
There is a vast difference in traditional web app security and web API security best practices – a difference that comes because of how they are structured.
A castle with no moat and multiple openings – Earlier, traditional networks only had to be protected in common ports like 443 (HTTPS) and 80 (HTTP). Today, web apps come with multiple API endpoints which use different protocols, so when an API expands its feature sets, managing its security gets difficult.
Frequently changing incoming request formats – APIs constantly evolve under a DevOps environment, most of the WAFs are unable to accommodate this extent of elasticity. Thus, whenever an API changes, the traditional security measures have to be reconfigured and tuned manually – an error-filled method that takes up resources’ time.
Clients may not use a web browser – A majority of the microservice APIs are used on mobile applications or software components. Because the clients do not use the browser, web security tools are unable to use the browser verification functionality and detect harmful bots.
This difference in API structure opens it up to several API security risks, deeming it critical for the web app developers and QA team to find solutions and improve API security in real time.
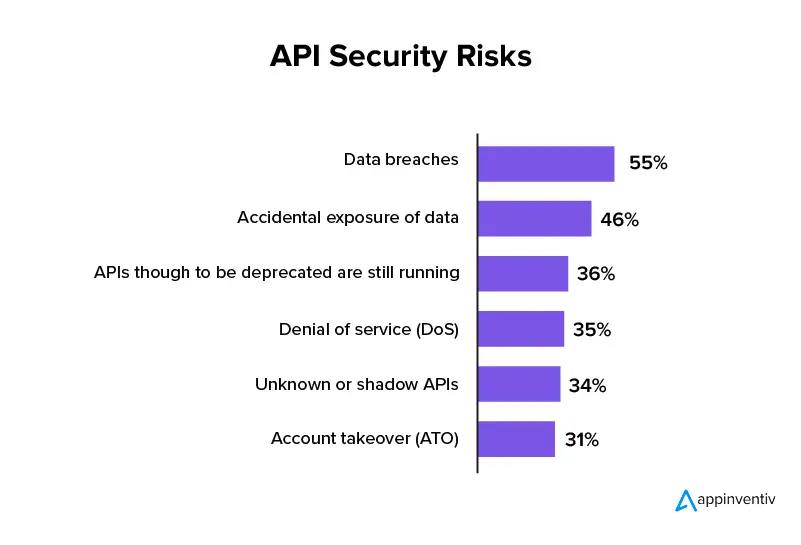
The top API security risks and how to mitigate them
Before we get down to the risks, let me tell you that the API security checklist is not definite. You think you have solved all the loopholes and new ones will come up. The solution to this lies in stepping in hackers’ shoes and relook at how your app uses API and the gaps that are overlooked.
While this a long-term, continuous solution, a good starting point will be to look into the most common API security risks.
1. Insecure pagination
Most of the APIs offer access to the resources which are the list of entities like users or widgets. For a client using the software on a browser, the API would typically filter out and paginate this list to restrict the number of items that are returned to the client.
However, if the entity comes with PII or some other information, a hacker would be able to scrape the endpoint and get a list of all the entities in the database. This can be very dangerous if the entities expose sensitive information accidentally. It will also lead to hackers being able to view your web app’s usage stats and get access to the email lists.
Solution: In order to secure against the pagination attacks, one should be able to track the number of items of a single resource which can be accessed within a specific time period by a user or an API key instead of at the request level. By measuring the API resource access at individual user level, you will be able to block the API key or user after they meet a threshold like “touched 10,000 items in one hour”.
2. Insecure API key generation
Most of the APIs are generally secured through JWT (JSON Web Token) or API key. This enables you to protect your API as the security tools are able to identify abnormal behavior and then block access to API keys. However, the hackers can still outsmart these approaches by getting and utilizing a massive pool of API keys from users, exactly like how a web hacker would make use of IP addresses to hinder DDoS protection.
Solution: The sure-shot way of securing these attacks is by needing a human to sign up for the service and then generate the API keys. On the other hand, the bot traffic can be saved with elements like 2-Factor Authentication and Captcha.
3. Accidental key exposure
The way API keys are used open it up to instances of hacks and leakages.
- The APIs are engineered to be obtained over an indefinite period, which raises the chances of a hacker obtaining an API key which has not expired.
- The user of an API comes with a direct access to the web app’s credentials like when debugging it through CURL or Postman. Following this, it only takes an accident for the developer to copy/paste the CURL command with the API key in a public forum such as Stack Overflow or GitHub Issues.
- API keys are typically bearer tokens that don’t require any identifying information. The APIs are not able to leverage elements like 2-factor authentication or one-time use tokens.
Solution: The way to safeguard key exposure is by using two tokens in place of one. Here, a refresh token gets stored as the environment variable and can be used for generating short lived access tokens. Unlike these refresh tokens, developers can use short lived tokens that can access resources, but only for a limited time period.
4. DDoS attacks
While it’s true that APIs open new business models where the customers can access the API platforms programmatically, this makes DDoS protection challenging. Most of the DDoS protection is engineered for absorbing and rejecting requests from bad actors during the DDoS attacks. This becomes harder in case of API products as every traffic ends up looking like bot traffic.
Solution: The API security best practices in this context lies within the API only. Every access to the web app requires an API key, so when you come across a request which doesn’t have an API key, you can reject it automatically.
5. Wrong server security
When it comes to maintaining good server hygiene, APIs are not very different from web servers. Data can easily be leaked because of a misconfigured SSL certificates or through non-HTTPS traffic.
In the case of modern-day web apps, while there is little reason to accept the non-HTTPS requests, a customer might accidentally issue a non-HTTP request from their web app or CURL, thus exposing the API key.
Solution: Best practices for API security state that you should test the SSL implementation over a SSL test tool. Moreover, you should block out the non-HTTP through the load balancer.
6. Insufficient logging
Most of the global breach studies find that the time period to identify a data breach instance is more than 200 days. If there is a lack of defined API security best practices for API logging in place, hackers can use the vulnerability to create more vulnerabilities.
Solution: You should make sure that the API logging mechanism you use doesn’t just track the API requests but also link it back to the users for behavior analysis and store it for at least a year. These mechanisms, in turn, should be secured to ensure that the data doesn’t get deleted.
7. Not handling authorization
While a majority of API developers add a global Authentication method like OAuth or API keys to verify who is the user, it is difficult to create and keep Authorization different from Authentication.
Since authorization is specific to the app’s logic, it is an area that developers miss on when testing the web app. Now, unless the object identifiers have sufficient entropy, hackers can easily test different ids via iteration and enter the system.
Solution: Make sure that the user you have authenticated is authorized to access resources needed for generating the API response. This may include checking it against access control lists (ACL) linked with the objects in the picture.
Here were the seven most common API security risks and their solutions that a web app developer and entrepreneur come across. But like we mentioned before, this list if not definite, many more loopholes can come up as your web app gets older and the API’s features expand.
At Appinventiv, when we build an API, we make a rough checklist for API security testing before the development process starts. In addition to this, we use the best API management tools that ensure your software is built for long-term robustness and security.

And here’s the API security checklist we follow.
Appinventiv checklist of API security best practices
What separates us as a web app development company is the fact that we follow a security-first development approach. Meaning, we are on top of your app’s security everytime we build or incorporate an API in it. Our team of QA specialists ensure that your web app doesn’t have any loopholes and is hack-proof. A way they ensure this is by creating a well-rounded checklist of API security best practices.
1. Find vulnerabilities
The primary way to improve API security is to identify the insecure areas of API lifecycle. What is necessary is to keep a track of it by treating APIs as software artifacts having their own development stages like maintenance and feature expiry.
2. Use OAuth
One of the biggest gaps in API security risks is accessing control of authorization and authentication. A powerful method of controlling that lies with OAuth. At Appinventiv, we use the token-driven authorization framework for allowing which information can be accessed by a third-party service without showing the user credentials.
3. Use tokens
Using tokens, in general, is one of the best API security best practices. The developers can make use of tokens allocated to identities as an effective way for establishing controlled access to trusted identities.
4. Data encryption
A sure-shot way to improve API security lies in encrypting data using Transport Layer Security (TLS). When we work on an API, we follow a practice where our developers also need signatures for ensuring modifications and decryption of data through an authorized user only.
5. Use rate throttling and limiting
With the APIs popularity constantly increasing, the probability of hacks like DDoS attacks are also increasing. To prevent DDoS attacks and API spikes like issues that impact security and performance, our developers place a rate limit on how and in what frequency an API can get called. This rate limiting functionality also throttles connections, balances data access with data availability.
6. Use API gateway
Using API gateways is what we deem to be one of the key API security best practices. It acts as API traffic’s point of enforcement. We build a gateway that enables businesses to authenticate the traffic, control and monitor how the APIs are being used.
7. Use service mesh
In addition to API gateways, we use service mesh to add a layer of management in the web app, as the service mesh routes the requests from one service to another. It also optimizes how the functions work together, while ensuring proper access control, authentication, and security measures are incorporated.
8. Zero-trust formula
In the traditional security model, the formula used is to be simple. What’s “inside” should be trusted and what’s “outside” should not be. However, networks have become complex now, because of which having a zero-trust model (ZTM) becomes important, especially since the software gets used by remote users. Through a ZTM, the focus of security moves from location to resources and users.
9. Validate parameters
Validating parameters is another one of our best practices for API security. It helps make sure that the incoming data is not causing any harm. Under the framework, the data gets validated against a stringent schema which reports the system of permissible inputs.
10. Build a threat model
The last in our checklist of ways to mitigate API security risks is threat modeling. It is an approach we use for finding and evaluating risks. We use it as a preventative approach to assess, mitigate, and prevent app vulnerabilities in a controlled fashion.
At the back of these API gateway security best practices, we are able to build a robust, secure system which the users can work on with complete confidence. The result? We come with a track record of creating apps with zero hack and security breach instances.
Parting notes
As businesses continue to transform their monolithic systems into microservices, APIs will keep getting prone to vulnerabilities. This makes following native and cloud API security best practices mandatory.
The list that we mentioned above, while is a good place to start, requires constant upgradation. Keeping on top of them can be a challenge for entrepreneurs and their in-house development teams which already juggles multiple deadlines. This is where partnering with a company that has a track record of delivering 100% hack-proof apps comes into picture. A company like Appinventiv.
No matter how complex your software is, we can make it secure and robust with our extensive quality assurance services. Get in touch with us today to kickstart your product’s secure future.


Excellence Together

How Much Does It Cost to Develop a Web App like Hukoomi?
According to a report, out of 8.1 billion of the estimated global population (measured on 14th Sept 2023), approximately 5.18 billion are internet users, meaning over 65% of the world's population uses web apps for various purposes. So, in an era where digital transformation is revolutionizing almost every aspect of the modern business world, the…

Website Development Cost Estimation in 2024: A Closer Analysis
Are you a budding entrepreneur looking forward to kickstarting your digital business or an enterprise looking to enhance its online presence through a well-performing website? If yes, you have landed at the right place. Being one of the most powerful marketing channels, a website can drive higher sales and enhance customer retention. It can further…