- Top 10 Cloud Security Risks in 2024, and How to Mitigate Them?
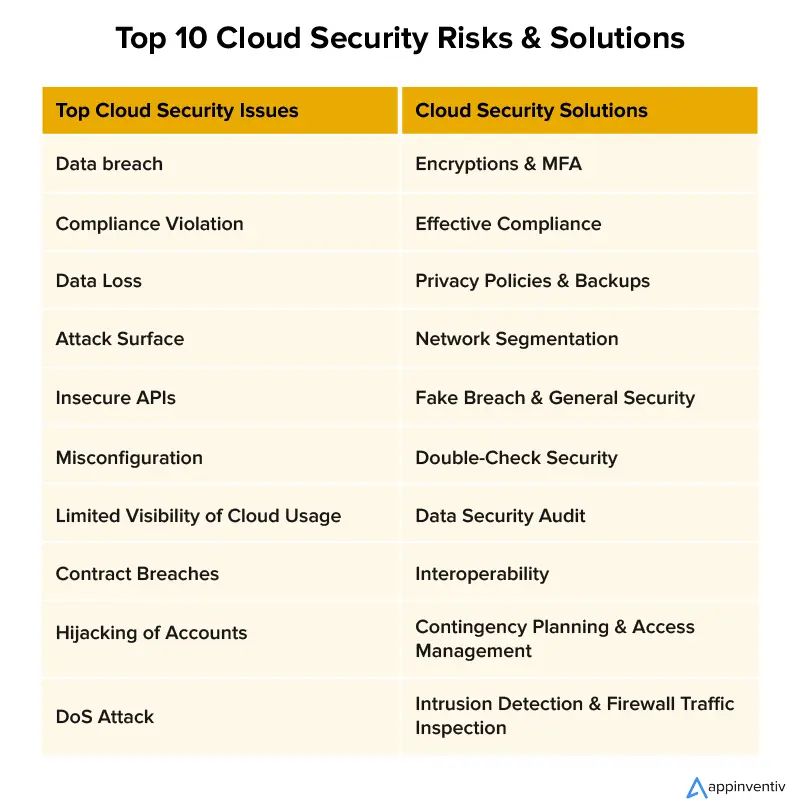
- 1. Data Breach
- What is the solution?
- What is the solution?
- 3. Data Loss
- What is the solution?
- 4. Attack Surface
- What is the solution?
- 5. Insecure APIs
- What is the solution?
- 6. Misconfiguration
- What is the solution?
- 7. Limited Visibility of Cloud Usage
- What is the solution?
- 8. Contract Breaches with Business Partners
- What is the solution?
- 9. Hijacking of Accounts
- What is the solution?
- 10. DoS and DDoS Attack
- What is the solution?
- Leverage Appinventiv’s Experience for Secure Cloud Services
- FAQs
If you’re still perplexed about why cybercrime is on the rise, consider the cause to be an economic slowdown. The recession is the result of increasing unethical cyber activities that have caused a huge loss to businesses. The truth is that an economic downturn encourages hackers to create new kinds of threats that are unavoidable.
If you haven’t been following the news, Silicon Valley Bank was closed down by the California Department of Financial Protection and Innovation following a bank run that was sparked by possible insolvency and a stock market decline. The major reason behind the SVB shutdown is cyber fraud potential. Therefore, it can be rightly said that data safety is crucial in terms of cloud security risks. Emphasizing on cloud has its own advantages, particularly in this era of recession.
Due to the nature of a remotely hosted server, cloud computing may add layers of risk for the users. The accessibility, size, and interconnectedness of data have now become incredibly susceptible to numerous cloud security risks.
As companies migrate their data to the cloud, security concerns such as accidental exposure of credentials and data loss have become more common than ever. Over the past few years, cyber threats have increased in number, making cloud security solutions essential for businesses.
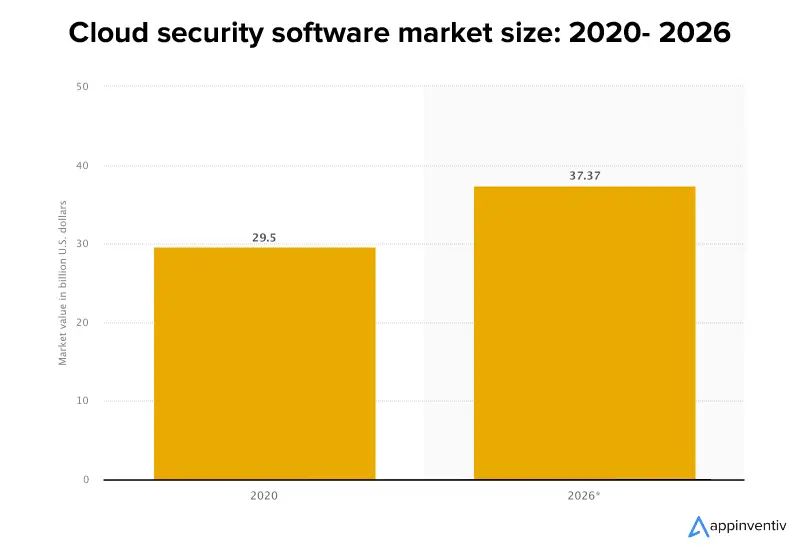
As reported by Statista, the global cloud security software market is expected to reach a valuation of $37 billion by 2026.
So, your organization must have a strong strategy to protect itself against cloud security threats and ensure business continuity. But to have a strong cloud security strategy, you must first be aware of the top cloud security issues and their possible solutions in 2024.
In this blog, we’ll talk about the security risks associated with cloud computing, along with helping you find the right tech partner for cloud consulting services that will let you boost its capabilities.
Let’s dive in!
Top 10 Cloud Security Risks in 2024, and How to Mitigate Them?
The way businesses store, utilize, and exchange data is constantly changing, thanks to cloud computing and security. The amount of sensitive data that is possibly at risk is growing as a result of increased cloud usage globally. Let’s check out the potential top cloud security threats 2024 and how to mitigate them:
1. Data Breach
When your organization’s confidential data is accessed and used without your knowledge or consent, we call it a data breach. It is basically a theft, which mostly happens due to weak credentials or highly complex accessibility systems, which can give wrong permissions to the wrong people.
It can also be due to the entry of malware into your system. In this, most attacks are directed at data systems, as this is what attackers value. Inadequate cloud configuration or no protection at runtime can leave data vulnerable to theft.
Different types of information have different consequences when compromised. Identity thieves and phishers purchase sensitive data like social security numbers and medical records from criminals on the dark web.
Internal documents and emails contain sensitive information that could be used to ruin a company’s good name and drive down its stock price if it fell into the wrong hands. Regardless of the motivation for the theft, breaches pose a serious risk to businesses that store data in the cloud.
What is the solution?
- Encryptions
With encryption, sensitive information can be safeguarded even before it leaves your company’s premises and goes to the cloud. Once your data is encrypted, you should hold on to the keys that can be used to encrypt and decrypt the data.
You should never keep encryption keys in the same program as your sensitive information. Besides ensuring they possess encryption keys, IT departments should regularly assess the efficacy of existing encryption protocols.
- Multi-factor Authentication
Users also need to provide credentials other than identification and access. For instance, entering a password and then getting a notification containing a one-time use key of numbers. These days, this is one of the standard requirements to mitigate cloud security issues. Read this blog to know how you can implement a multifactor authentication system in your mobile app.
2. Compliance Violation
Companies run a high risk of severe consequences if they fall into a state of non-compliance. Regulations like PCI-DSS that protect sensitive data must be utilized by all organizations.
[It might interest you to read how you can create a PCI DSS-compliant application]
Compliance with these regulations may require you to create an isolated part of the network that is only accessible by authorized staff members. Many organizations restrict access and what individuals can do when given access to ensure compliance standards are followed.
If compliance regulations are not followed, the business might face penalties and fines, which can harm the business. Unfortunately, not all cloud service providers adhere to all security standards set by the industry. A significant problem arises when a cloud-based service is added without checking its compliance with all applicable legal standards.
What is the solution?
- Ensure effective compliance
Most businesses have implemented privacy and compliance policies to safeguard their resources. Furthermore, a governance framework should define roles and responsibilities inside the business and ensure that these rules comply.
Note each employee’s roles and responsibilities in a set of policies. It must also specify how they communicate with one another.
3. Data Loss
Losing data is the biggest risk, that is, at most times, irreversible. The data can be lost due to various reasons – the open databases, storage on the non-dependable cloud storage service provider, losing or deleting the data accidentally, or losing your credentials to access the data.
Our extensive guide on Data Loss Prevention and its best practices can help you understand various security constraints and how to approach them.
Though a great benefit and essential to cloud-based collaboration is the simplicity with which you may share information via the cloud. However, it gives rise to significant privacy and security issues in cloud computing, which is the main reason why businesses move to the cloud. When sharing information via public links or a cloud-based repository is set to public, anybody with the link can access it. There are tools designed to scour the web for such insecure cloud deployments.
What is the solution?
- Enforce Privacy Policies
The success of any business depends on its ability to keep private and sensitive data safe. An organization’s storage of personally identifiable information is vulnerable to hacking and other forms of security breaches. When a cloud service provider needs to provide sufficient security safeguards, businesses should either go elsewhere or refrain from storing any sensitive data with them.
- Backups
The best approach to security risks of cloud computing is to prevent data loss through regular data backups. You need a schedule for backing up the data and a precise definition of what data will be backed up and what will not. For automation, use data loss prevention software.
[Also Read: How can enterprises protect their data in cloud environments?]
4. Attack Surface
What we call an environment’s overall vulnerability is called its attack surface. The attack surface grows with each new task. In some cases, the amount of openly accessible workload can increase after microservices are used. If you don’t keep it well-managed, your infrastructure may be vulnerable in ways you are unaware of once it is attacked.
A call at this hour is the last thing anyone wants.
Subtle information leaks that open the door to an attack also constitute part of the attack surface. Because of the inherent nature of the internet and the cloud, you always leave yourself vulnerable to outside attacks.
It could be crucial to the daily functioning of your company, but you should keep an eye on it.
What is the solution?
- Proper Network Segmentation and Security
Create security zones in each of your environments and only allow traffic that is necessary and authorized to pass past the firewall. If possible, provide each application environment (development, staging, and production) its own cloud account.
- Leverage the Principle of Least Privilege
With purpose, provide access and resources. For example, a developer who is merely deploying code shouldn’t have administrative access to the entire cloud account. A developer shouldn’t also have constant access to a working environment. Just provide them with what they require. Tools are available to aid in properly sizing accounts and users.
5. Insecure APIs
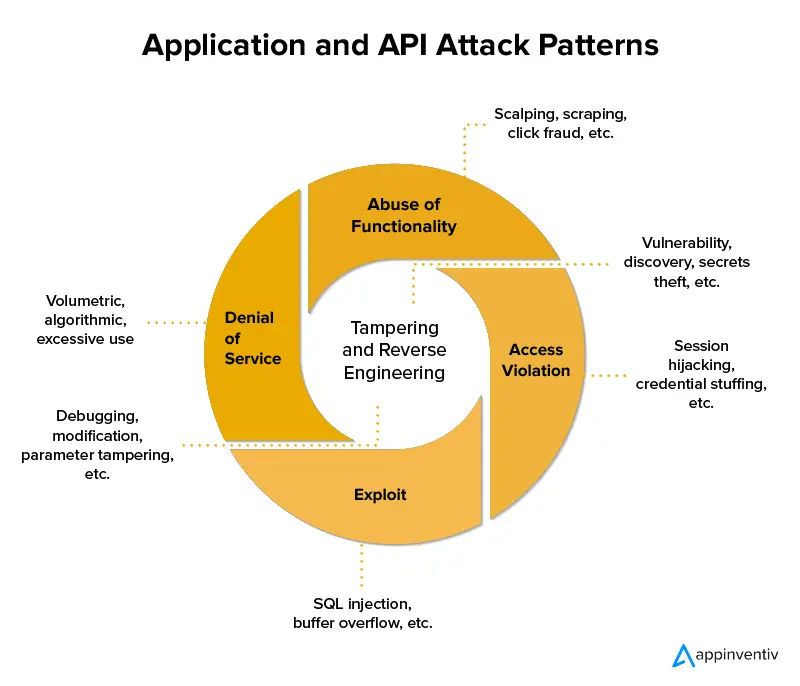
Apart from allowing businesses to customize their cloud service, application programming interfaces or APIs also enable access, authentication, and encryption. As APIs advance to better serve users, they also pose a greater security risk to the data stored.
Your data and systems could be compromised if you rely on cloud services using unsecured APIs. Usually, these are well-documented for the ease of usage of customers, but if not appropriately secured, they can cause critical issues. Hackers typically employ one of three methods to break into an API: brute force, distributed denial of service, or man in the middle. Your cloud security solutions must be able to tackle these three methods.
What is the solution?
- Fake Breach
Penetration testing that simulates an external assault on a set of API endpoints to breach the security and gain access to the organization’s confidential data will give you an idea of how secure the system is and what improvement is needed.
Assessment of General System Security
The regular audits that you should do must include checking the system and its layers of security to ensure it won’t let anyone break into the APIs.
In case you wish to get further insights into how to tackle API security risks, hop on to our blog, the top API security risks and how to mitigate them.
6. Misconfiguration
As time goes on, more and more services will be made available on a cloud environment. Today, it’s common for businesses to work with multiple vendors.
Each service has a unique implementation that can vary greatly from one provider to the next. Threat factors will continue to take advantage of security flaws in cloud infrastructure unless and until businesses improve their cloud security practices.
What is the solution?
- Double-Check your Security
When setting up a specific cloud server, double-check the settings for cloud security. Often, double-checking security is ignored in favor of more pressing matters like putting goods in storage without giving the security of their contents a second thought.
7. Limited Visibility of Cloud Usage
When information and assets are transferred to the cloud, some visibility and control over these assets are lost. Limited visibility can be a cause of data breaches and data loss because it opens risks that are linked to poor governance and lack of security. The worst part is that these blind spots do not allow a timely alert when security issues, breaches, performance, or compliance problems occur.
What is the solution?
- Data Security Audit
Find out if your cloud service provider regularly audits the security controls in place to safeguard the personal data and sensitive files stored by end users across their networks. If they don’t, look elsewhere for a partner who can provide full transparency regarding the security measures implemented by their system administrators.
- Risk Assessment and Analysis
You must do a risk assessment at regular intervals to keep a check on potential risks. Make sure you also have a plan in place to mitigate these risks that arise out of partial transparency.
8. Contract Breaches with Business Partners
Both, The use of data and the individuals who are permitted access to it are limited by the terms of contracts between businesses and their customers. By storing business information in personal cloud storage, employees put their employer and themselves in danger of legal action.
Confidentiality clauses in commercial contracts often break. And this is especially true if the cloud provider reserves the right to disclose any and all submitted data to any interested party.
What is the solution?
- Interoperability
Make sure your vendors can cooperate when you source several cloud providers for the same services. Don’t forget to include coverage for data transfer after termination. A lack of standardized data standards can make data movement between clouds laborious. It is crucial to ensure timely and reliable access to your data and to define your obligations in relation to those of your provider.
- Data Security
Terms laid down in contracts should take into account internal and external attacks as well as human mistakes. It is sometimes necessary to take into account that a breach caused by a disgruntled employee may be worse than one caused by an outside attack.
9. Hijacking of Accounts
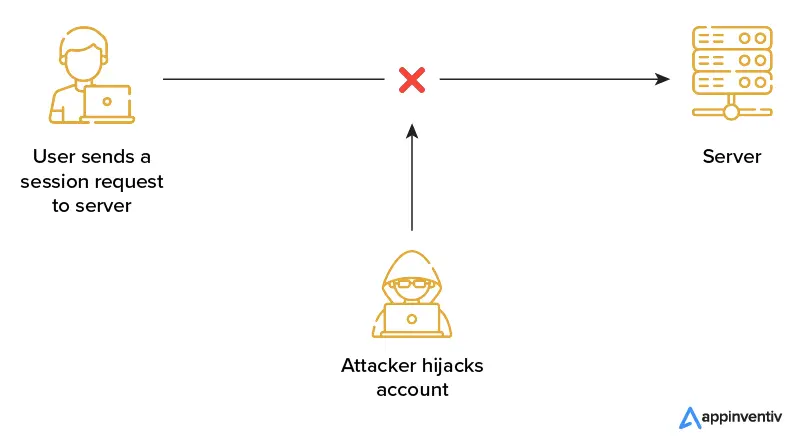
Password reuse and simple passwords are only two examples of poor password hygiene that plague many people. Since you can use a single stolen password across several accounts, this issue magnifies the damage done by phishing attacks and data breaches.
As businesses rely more on cloud-based infrastructure and apps, account hijacking has become a major threat to cloud security. Suppose an attacker gains access to an employee’s credentials. In that case, they may have access to sensitive information or capabilities, and if a customer’s credentials are compromised, the attacker gains complete access to the customer’s online account. Also, unlike on-premises infrastructure, cloud environments sometimes provide different visibility into and control over security concerns.
What is the solution?
- Contingency Planning
In the event of any major emergencies, such as natural disasters or terrorist attacks, you need your risk management in cloud computing to play. Make sure your online storage provider has a business continuity plan that outlines its strategy for protecting information stored within its servers. Ask them how frequently they test these security concerns in cloud computing to make sure everything functions properly.
- Access Management
Set a distinct layout of access management. The layout of access management defines the information’s accessibility for various users. For instance, the quality assurance department’s protocols shouldn’t be accessible to the marketing department and vice versa.
10. DoS and DDoS Attack
DoS is likely to happen in outdated systems that get overwhelmed with data and stop functioning properly because of the overload. It is not really synonymous with hacking but the outcome of such an attack is that it renders the system unusable or inaccessible.
The denial-of-service attack’s goal is to prevent users from using the programs or interfering with their workflow. The two main categories of DoS attacks are:
- Forceful attacks from various origins
- Complicated attacks aimed at exploiting system processes such as content delivery
System resources are wasted during a DoS attack, which can result in a number of speed and stability issues. It makes it difficult to load applications or makes it difficult to pinpoint the source of disruption.
Also, you need to be aware of DDoS, whereby cybercriminals bombard a network with so much malicious traffic that it is unable to function or communicate as it typically would. This stops the site’s regular activity, also referred to as legitimate packets.
What is the solution?
- Intrusion Detection System
Businesses utilize intrusion detection systems to protect against DoS assaults. According to the user’s credentials and behavioral variables, this system assists in identifying unusual traffic and provides an early warning. It is often referred to as a break-in alert for cloud security risk management.
- Firewall Traffic Inspection
Examining incoming traffic through a firewall to determine its origin or to identify good or harmful traffic in order to aid in traffic sorting and the elimination of unwanted traffic can help prevent DoS. Blocking the IP addresses that could launch an assault also aids in preventing a DoS attack.
Leverage Appinventiv’s Experience for Secure Cloud Services
At Appinventiv, we understand the need for secure cloud computing services with a sturdy architecture that does not easily break down. Our in-house team of expert engineers and designers has gained immense experience in delivering 200+ cloud-based application deliveries managing and designing robust cloud architectures for multiple international brands.
For instance, we developed a secure cloud-based ERP solution for one of the biggest furniture retailers, IKEA. While working on a private IP address, we created a solution that enabled every store to work independently while staying collaborative.
Similarly, by providing a secure cloud-based data analytics services solution, we enabled the leading telecom service provider with a solution that reduced their hardware and maintenance costs by 26%.
With a team of certified cloud professionals that work with a mission of constant innovation, providing mature solutions, get a reliable and secure cloud solution to eliminate all cloud security issues. We provide complete access to all of your cloud data in real-time and offer a scalable solution to your cloud. The cloud will also support all major integrations, which can help you reduce a variety of cloud computing security risks.
FAQs
Q. How can organizations ensure the security of their data when using cloud services?
A. Given its increasing prevalence, understanding the need for greater accountability in cloud usage is crucial. However, before making the switch, companies must think strategically about how they will use this technology and what they hope to accomplish.
By availing the latest cloud managed services, businesses can scale and adapt quickly, drive business agility, accelerate innovation, modernize operations, and cut expenses. This can not only help businesses get through the present crisis, but it can also result in more robust long-term growth. Read this complete guide on cloud computing to know more.
Q. How to manage cloud security risks?
A. Here are some of the tips to manage cloud security risks:
- Identify new risks of cloud computing and perform regular risk assessments.
- Document and reevaluate any risks you decide to accept.
- Prioritize and implement security controls to reduce the risks you’ve found.
Q. What essential questions should I ask my cloud service provider regarding cloud security risks and measures?
A. While the questions can vary as per your requirements, use the following questions as a guide:
- What are specific data transmission encryptions included in the cloud?
- Where are the servers physically located?
- Who can access the data in the cloud?
- What action will be taken in case of security violation?
- How are GUIs and APIs protected?
- What level of technical support is available?
- What is my company’s role in data protection?
Q. What workload should I shift to the cloud?
A. You could move any workload to a cloud architecture. To meet all necessary regulatory compliances, you will need to pay particular attention to the implications of cloud migration and that its architecture keeps your data secure. Get in touch with a reputed cyber security consulting firm to know more.


Excellence Together
Is a Cloud-Native Application Protection Platform (CNAPP) the Answer to Security Woes?
Cloud computing, at the back of its wide-ranged benefits spanning across scalability, high mobility, easy data recovery, high performance, and quick deployment, has come at a stage where the market is set to reach $676 billion in 2024. While on one side, the idea of having on-cloud presence is becoming mainstream, the other side -…
On-premise vs. cloud - Analyzing the benefits, risks and costs for enterprises
Are you standing at the crossroads of a technological revolution, pondering the question that's on every modern enterprise's mind: on-premise vs. cloud? The stakes are higher than ever. With the global cloud computing market poised to soar to an astonishing $2.3 trillion by 2032, the future seems to be whispering its secret preference. Yet, the…








